
Students hate being graded. Wouldn’t life be easier, many wonder, if we could grade ourselves?
Infosec pros from around the world have been given that chance by Domain Tools, who today released their second annual self-assessed cyber security report card.
Assuming there’s honesty in anonymity, and the sample survey of 525 respondents from companies ranging in size and geography is representative, there are some signs of progress.
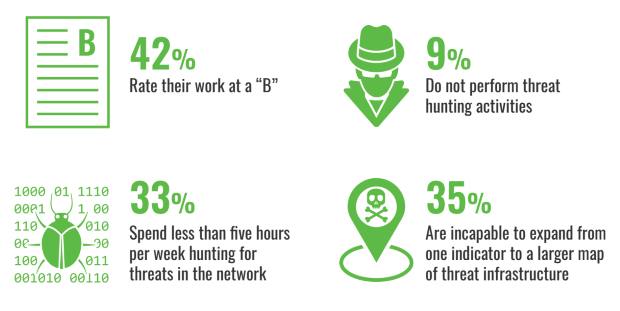
“Overall, report card grades improved in 2018, with 21 per cent of respondents giving their programs an “A,” (up from 15 per cent) and 42 per cent rating their work at a “B,” says the report.
“Use of automation, improvements in employee security training and a 10 per cent increase in the use of threat intelligence tools contributed to the boost in confidence.”
Also, the number of people that responded “I don’t know” when asked, “Which tools do you use as part of your organization’s defense approach?” decreased by about five per cent, “demonstrating a gradual improvement in program development,” says the report author.
Strategic use of automation technology plays a significant role among highly-rated programs, the report found. So much so that 92 per cent of companies rating themselves as “A” said they use automation to simplify time-consuming processes. Conversely, “D” and “F” companies said their processes are highly manual. When compared to last year, there was an eight per cent decrease in the number of teams using manual processes and an increase among groups considering automated solutions.
Five per cent more organizations plan to step-up security awareness training in the coming year than did last year, and the number of those that intend to skip training initiatives decreased by half from 2017.
However, “one surprising finding,” says the report, “was the decrease in malware analysis when investigating attacks. Malware
analysis declined by 12 per cent from 2017, and forensic analysis of compromised machines was scaled back by six per cent.” One potential reason for this, the report speculates, is that malware analysis tends to be a manual and time-intensive process.
Arguably just as worrisome is that 35 per cent of respondents admitted they don’t have the capability to expand from one threat indicator to a larger map of threat infrastructure, In fact one-third said they spend less than five hours per week hunting for
threats in the network.
Another interesting finding: 60 per cent said their organization has a formal training program for security staff. About 35 per cent said they’re planning to add one next year. Roughly 15 per cent of respondents said their firm doesn’t need a formal training program.
Finally, when asked what it would take for their organization to become an “A,” half said it would take a bigger budget, with about 45 per cent saying they’d need more staff, or more time to evaluate new technologies or increased automation.
Source: itworldcanada.com
Author: Howard Solomon
